Installing Config Server Firewall (CSF) on Debian / Ubuntu

Config Server Firewall ConfigServer and Security firewall, abbreviated CSF, is an open source and advanced firewall designed for Linux systems. Not only does it provide basic firewall functionality, but it also offers a wide range of advanced features such as logon / intrusion detection, exploit scans, death protection ping, and more.
[ You might also like: 10 Useful Open Source Security Firewalls for Linux Systems ]
In addition, it also provides interface integration with widely used control panels such as cPanel, Webmin, Vesta CP, CyberPanel and DirectAdmin. For a complete list of supported features and operating systems, visit ConfigServer’s official website.
In this guide, we will guide you through the installation and configuration ConfigServer Security & Firewall (CSF) on Debian and Ubuntu.
Step 1: Install CSF Firewall on Debian and Ubuntu
First, you need to install some dependencies before you start the installation CSF party wall. Update the package directory in your terminal:
$ sudo apt update
Next, install the dependencies as shown:
$ sudo apt install wget libio-socket-ssl-perl git perl iptables libnet-libidn-perl libcrypt-ssleay-perl libio-socket-inet6-perl libsocket6-perl sendmail dnsutils unzip
Once it’s out of the way, you can move on to the next step.
Since CSF not included by default Debian and Ubuntu archives, you need to install it manually. Please continue downloading CSF tarball, which contains all the installation files with the following wget command.
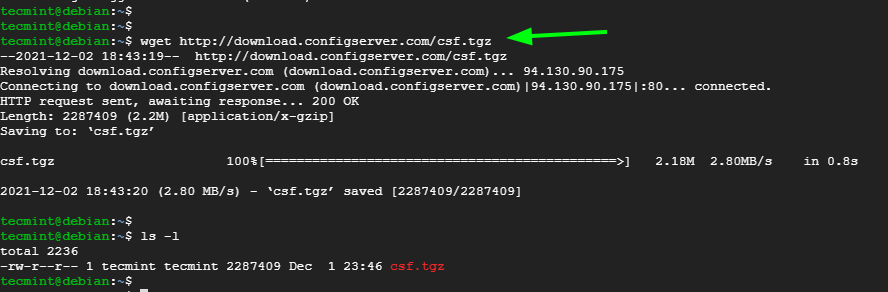
$ wget http://download.configserver.com/csf.tgz
This will download the compressed file named csf.tgz.
Next, extract the compressed file.
$ tar -xvzf csf.tgz
This will create a folder named csf.
$ ls -l
Go to the next step csf folder.
$ cd csf
Then install CSF Firewall by running the displayed installer.
$ sudo bash install.sh
If all went well, you should get the result as shown.
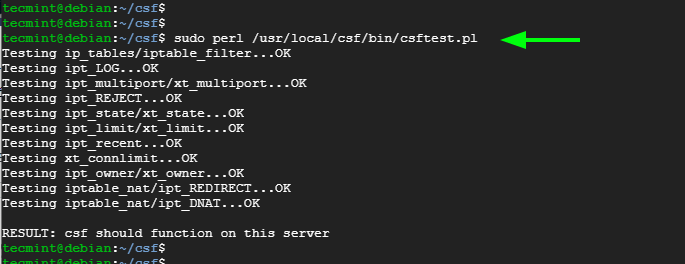
In this situation, CSF has been installed. However, you need to make sure that the required iptables are loaded. To do this, run the command:
$ sudo perl /usr/local/csf/bin/csftest.pl
Step 2: Configure the CSF firewall in Debian and Ubuntu
Some additional configuration is needed Next, we need to change a few settings to enable them CSF. So head towards csf.conf settings file.
$ sudo nano /etc/csf/csf.conf
Edit TESTING help from “1” towards “0” as shown below.
TESTING = "0"
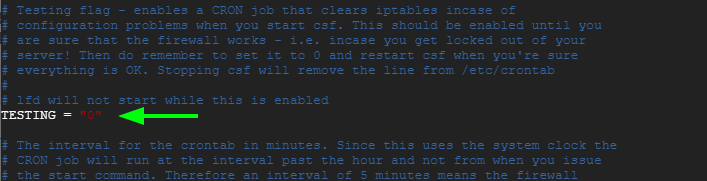
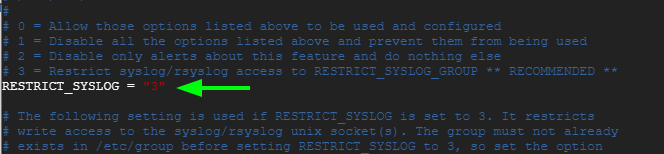
Set next RESTRICT_SYSLOG guide “3” to restrict rsyslog / syslog access to members only RESTRICT_SYSLOG_GROUP.
RESTRICT_SYSLOG = "3"
Next you can open TCP and UDP searching for gates TCP_IN, TCP_OUT, UDP_IN, and UDP_OUT Directive.
By default, the following ports are opened.
TCP_IN = "20,21,22,25,53,80,110,143,443,465,587,993,995" TCP_OUT = "20,21,22,25,53,80,110,113,443,587,993,995" UDP_IN = "20,21,53,80,443" UDP_OUT = "20,21,53,113,123"
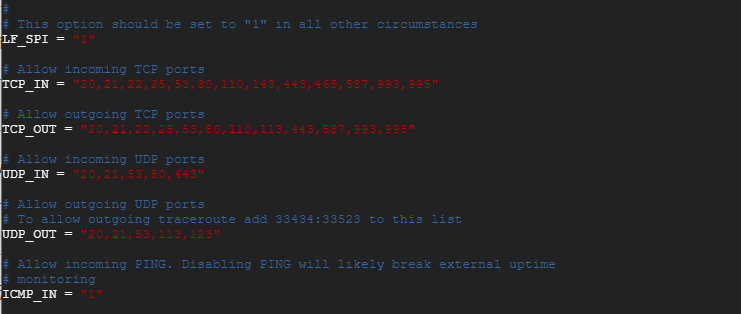
You may not have to open all the ports, and best server practices require that you only open the ports that you use. We recommend that you delete any unnecessary ports and leave the ones used by the services on your system.
Once you have configured the ports you need, reload CSF as shown.
$ sudo csf -r
To list all the IP table rules assigned to the server, run the command:
$ sudo csf -l
You can start and enable CSF firewall at startup as follows:
$ sudo systemctl start csf $ sudo systemctl enable csf
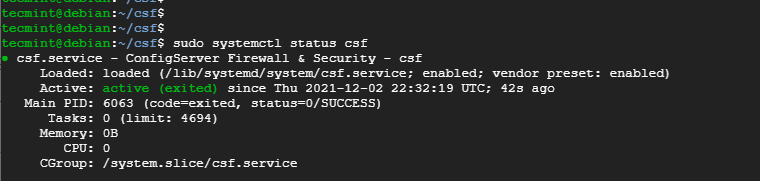
Then make sure the firewall is running:
$ sudo systemctl status csf
Step 3: Block and allow IP addresses in the CSF firewall
One of the most important functions of a firewall is the ability to allow or block IP addresses from accessing the server. With CSF, you can add to the whitelist (allow), black list (prohibit) or bypass IP addresses by editing the following configuration files:
- csf.allow
- csf.deny
- csf.ignore
Block the IP address in the CSF
To block the IP address, use csf.deny settings file.
$ sudo nano /etc/csf/csf.deny
Then specify the IP addresses you want to block. You can configure IP addresses line by line as shown:
192.168.100.50 192.168.100.120
Or you can use CIDR entry to block the entire subnet.
192.168.100.0/24
Allow IP address in CSF
To allow an IP address through Iptables and exclude it from all filters or blocks, edit csf.allow settings file.
$ sudo nano /etc/csf/csf.allow
You can list the IP address per line or use CIDR address, as previously shown when blocking IP addresses.
NOTE: An IP address is allowed even if it is specified csf.deny settings file. To make sure an IP address is blocked or blacklisted, make sure it is not listed csf.allow file.
Exclude the IP address from the CSF
In addition, CSF allows you to exclude an IP address from IP tables or filters. Any IP address csf.ignore the file is released from the iptables filters. It can only be blocked if specified in csf.deny file.
To exclude an IP address from filters, open csf.ignore file.
$ sudo nano /etc/csf/csf.ignore
Once again, you can list IP addresses line by line or use CIDR entry.
Conclusion
And this concludes our guide today. We hope you can now install and configure CSF firewall without bugs.




